Security seems to always be a hot-potato topic so today I'll be writing about taking advantage of the security development tool in AX2012.
The menu path to access the tool is System administration > Setup > Security > Security entry point permissions:
There are a myriad of powerful different techniques to leverage this tool. The three (3) I intend to focus on for this brief update are as follows:
- Identify a security role's current access level for a particular menu item.
- Identify security duty(ies) or security privilege(s) for a particular menu item, form, or element within a form.
- Viewing permissions associated to an executed task.
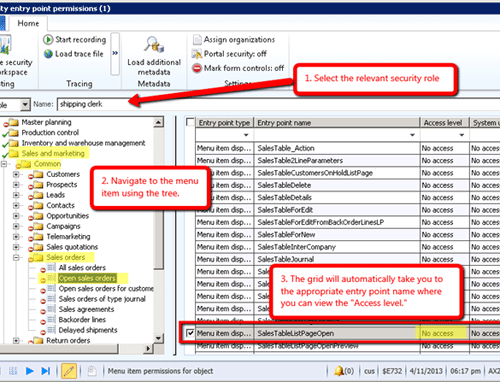
1) Identify Access Level
Identify a security role's current access level for a particular menu item, form, or element within a form.
- Select the relevant security role
- Navigate to the menu item using the tree
- The grid will automatically take you to the appropriate entry point name where you can view the "access level."
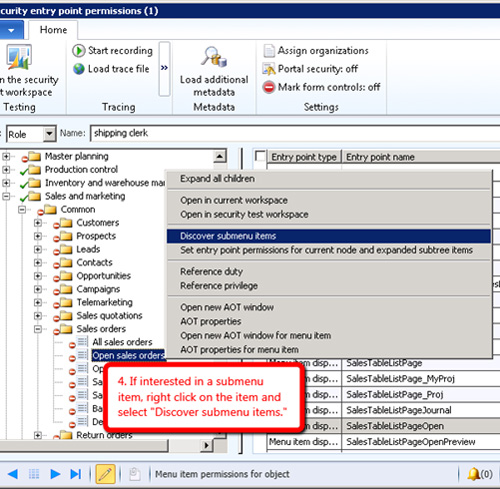
- If interested in a submenu item, right click on menu item and click on "Discover submenu items"
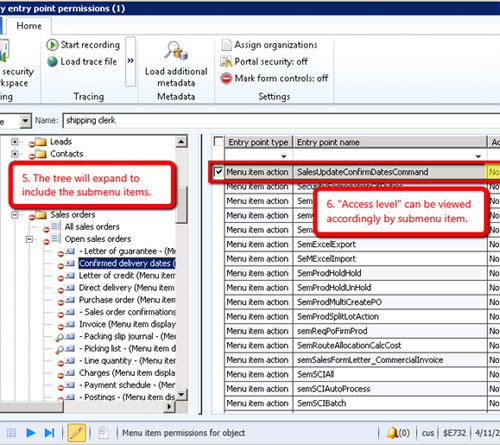
- The tree will expand to include the submenu items
- "Access level" can be viewed accordingly by submenu item
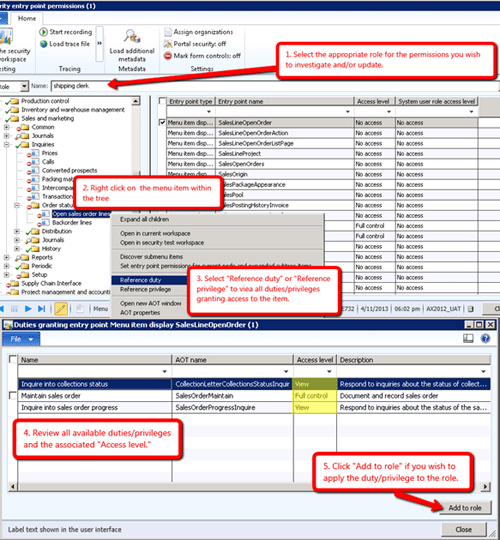
2) Identify Security Duties and Privileges
Identify security duty(ies) or security privilege(s) for a particular menu item, form, or element within a form.
- Select the appropriate roll for the permissions you wish to investigate and/or update
- Right click on the menu item within the tree
- Select "Reference Duty" or "Reference Privilege" to view all duties and privileges granting access to the item
- Review all available duties/privileges and the associated "Access level"
- Click "Add to role" if you wish to apply the duty/privilege to the role
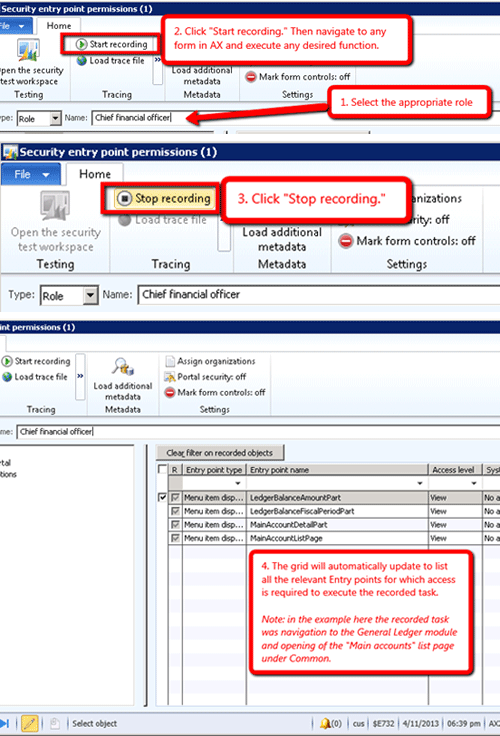
3) Task Permissions
Viewing permissions associated to an executed task:
- Select the appropriate role
- Click "Start recording." Then navigate to any form in AX and execute any desired function
- Click "Stop recording"
- The grid will automatically update to list all the relevant entry points for which access is required to execute the recorded task. Note: in the example here the recorded task was navigation to the general ledger module and opening of the "Main accounts" list page under Common.
Hopefully you will be able to leverage these tips to help answer the question, "What access does the user need?" Such questions will inevitably be awaiting each of you in the projects ahead.
Additional features exist within this tool to further leverage configuration and update changes to the security roles, privileges, and duties in AX. Nonetheless, the aforementioned features will give you the information you need to hone and tweak security to the client's content.









